By: Denekew A. Jembere
 Licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
Licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
In the current dynamic and challenging cyber era, organizations are required to have an effective information technology (IT) governance strategy with appropriate IT policies, standards, guidelines, and procedures for the effective and secure use of IT. In the effective IT policy management practices, universities could play a significant role by spearheading and showcasing a practical design and implementation of university-focused technology policies. With university-focused IT policies, universities could provide practical policy exposure and experience to their students, improving the entrepreneurial and innovative outcomes of technology transfer to industries (Cunningham et al., 2019; Han, 2018). However, effective management of IT policies has challenges (Umaroh & Kartika, 2018) and would require using an IT policy management framework that could facilitate the effective creation, implementation, monitoring, and storage of the IT policies. Therefore, this paper outlines an IT policy management framework that simplifies the creation, storage, approval, modification, and removal process of IT policies for an educational institution, Addis Ababa University (AAU), in Addis Ababa, Ethiopia.
The State of IT Policy Management at Addis Ababa University
Addis Ababa University (AAU, n.d.-a), established in 1950, is the oldest and the largest higher learning and research institution in Ethiopia (AAU, n.d.-b). According to AAU (n.d.-b), the university currently has more than fifty thousand students enrolled in 70 undergraduate, 221 masters, and 72 Ph.D. programs in its 14 campuses across Addis Ababa, the capital of Ethiopia. With its more than 8,700 academic and administrative staff and the increasing student population, the university’s population could easily get to 60 thousand in a regular academic year. The university has academic programs focused on IT, and most of its administrative activities are IT-supported. However, no IT policies, standards, guidelines, and procedure documents are available and accessible from the university’s public website. Therefore, using an IT management framework could benefit the AAU to govern its IT resources effectively and efficiently through the creation, storage, approval, modification, and removal of pertinent IT policies required by the different units of the university.
The IT Policy Management Framework
The IT policy management framework, outlined in this paper, has three components: the IT policy design decision flow chart, the IT policy evaluation tool (ITPET), and people (represented by roles and responsibilities of individuals or offices). Each of these components is outlined in the subsequent sections. The integration of these three components facilitates the proper execution of the IT policy management framework steps (Alkhaldi et al., 2017) outlined in The IT Policy Management Framework in Action section.
The IT Policy Design Decision Flow Chart
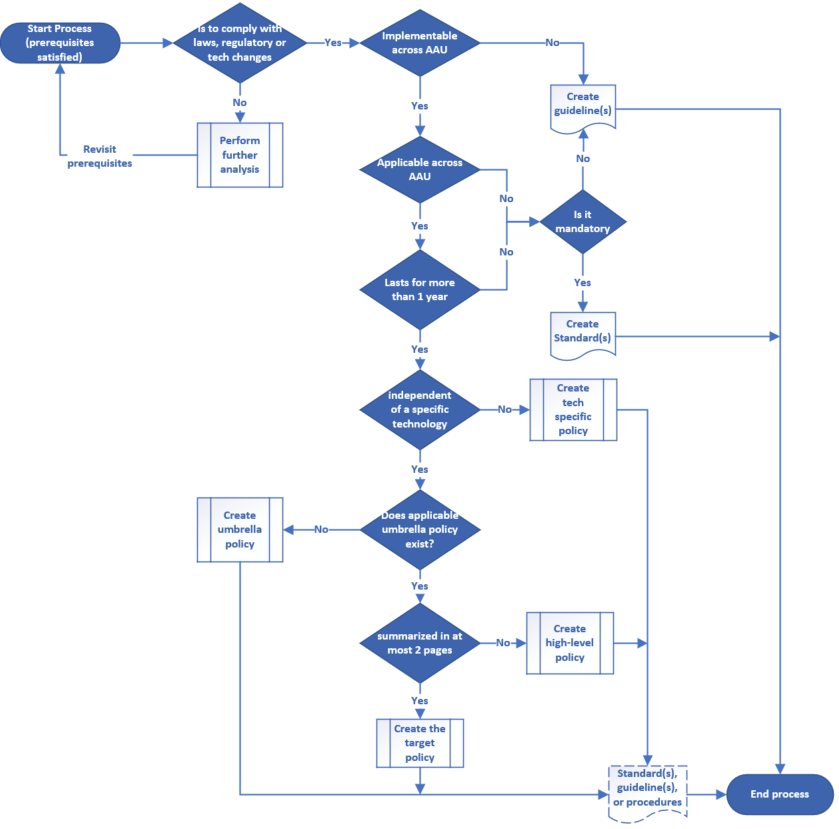
For a consistent IT policy development process, there are steps and decision points that the IT policy development team should follow. The decision flow chart in Figure 1 facilitates the process by enabling the policy development team to determine if a policy, standard, guideline, or procedure is required. However, for using the decision flow chart, at least one of the following prerequisites should be satisfied:
- There is a legal requirement to have documented guidance.
- There are operational issues that require a clear statement of direction or policy.
- A new technology (such as cloud computing) or technological change requires university-wide documented direction or policy.
- Documenting or implementing guidelines mitigates potential risks.
The IT Policy Evaluation Tool (ITPET)
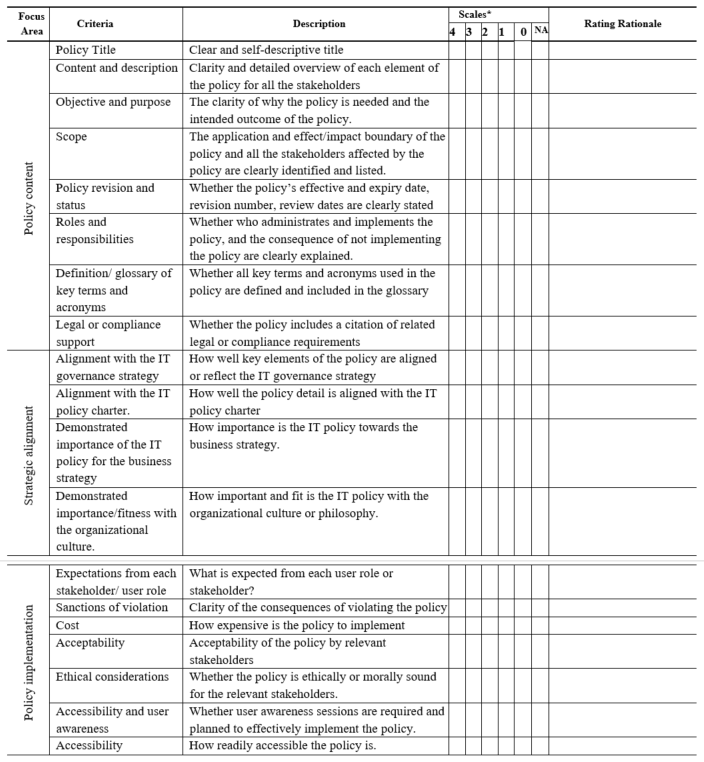
An IT policy can be evaluated using three categories of criteria: content, implementation, and strategic alignment (Alaceva & Rusu, 2015; Gover et al., 1996; Siregar et al., 2018; Tanaka & Sakata, 2017). The policy content evaluation criteria focus on evaluating the policy using key elements expected to be available in the policy document as metrics. The policy implementation evaluation criteria evaluate the policy details from the implementation perspective. The strategic alignment criteria focus on evaluating the IT policy about the policy’s strategic importance to business and its fitness to the organizational culture or philosophy. The IT policy evaluation tool (ITPET), with the specific and detailed criteria of the three criteria categories (content, implementation, and strategic alignment), is shown in Table 1
Table 1
IT Policy Evaluation Tool (ITPET)
The IT Policy Related Roles and Responsibilities
To facilitate the explanation of an IT policy management framework identifying the roles and responsibilities of individuals and offices most directly involved in the IT policy management process is essential. In this regard, the following roles and responsibilities, adapted from Northcentral University (NCU, n.d.) and the University of Michigan (UM, n.d.), representing the positions of individual and offices involved in the IT policy management process, will be used to explain the IT policy management framework usage.
- IT Policy and Compliance Officer (ITPCO) – provides the overall direction and day-to-day staff support for the IT policy function, participates in policy development working groups, and plans and executes IT policy training and communication efforts. In addition to ensuring appropriate stakeholders’ involvement in policy development, conducting research to identify and prioritize policy needs, the ITPCO leads the monitoring, annual review, and analysis of existing policies, standards, and guidelines for continued pertinence and effectiveness.
- Vice President of Information Technology (VP-IT) – has overall responsibility for IT policy and policy development and approves new and revised standards and guidelines based on the VP-Cybersecurity recommendation.
- Vice President of Cybersecurity (VP-Cybersecurity) – works with ITPCO to ensure alignment of the IT Policy program with Office of the VP-IT and the university’s strategic directions and priorities.
The IT Policy Management Framework in Action
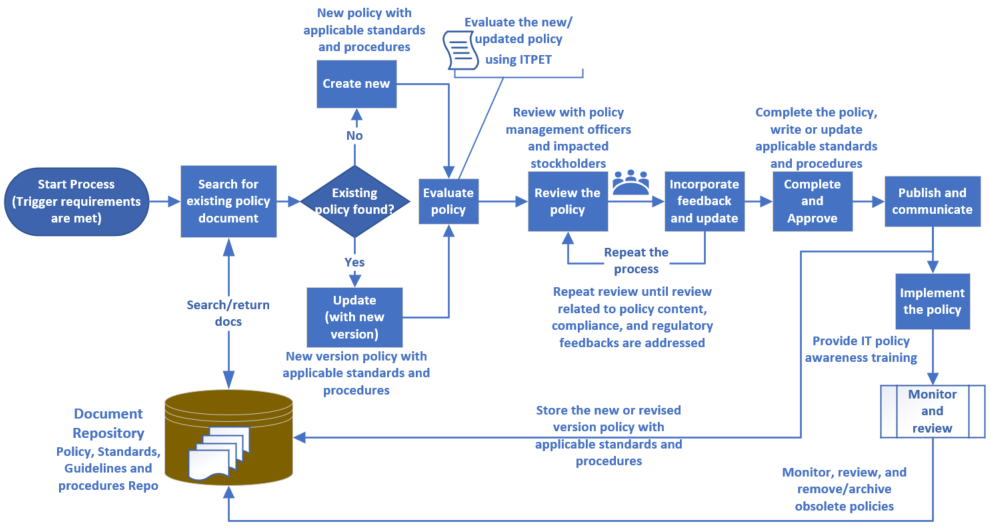
In this section, the use of the IT policy management framework, shown in Figure 2, and its dependency on the two components, the IT policy design decision flow chart and the ITPET is outlined in action by the people and offices with roles and responsibilities, outlined in earlier sections.
Create New or Update an Existing IT Policy
This step is triggered in response to new regulatory requirements, technology developments, operational needs, and identification of current issues or gaps identified by the ITPCO or requested by a university unit. Concerning the request, if there is an existing policy repository, which supports searching for a policy using predefined policy metadata (such as policy title, policy number, and other standard tags), then the ITPCO searches for a related policy for the requirement at hand. If an existing policy can be revised to incorporate the latest requirements, the ITPCO creates a copy of the policy and proceeds to the next step; otherwise, create a new policy for the new requirement. If an existing policy is to be revised and published with a new revision number, the ITPCO archives the old version of the policy at the monitoring and review step of the policy development process.
Evaluate the IT Policy
Once a new IT policy is created from scratch or based on an existing IT policy, to address the policy requirement, the ITPCO performs a preliminary evaluation of the IT policy using the IT evaluation tool (ITPET), which is detailed in the IT Policy Evaluation Tool (ITPET) section. This step focuses on content, implementation, and strategic alignment evaluation of the IT policy and could optionally involve the VP-Cybersecurity for ensuring alignment with the university’s strategic directions and priorities.
Review the IT Policy and Incorporate Feedback
For reviewing the IT policy, ITPCO invites the VP-Cybersecurity and representatives of appropriate stakeholders impacted by the policy implementation. At this step, the ITPCO presents pertinent justification related to gaps, risks, or research findings to ensure the IT policy’s need. This step’s execution ensures the IT policy content to be thorough from compliance regulatory and gaps expected to be addressed by the policy and involves repeated review and feedback incorporation updates.
Complete and Approve the Policy
At this step, the ITPCO and VP-Cybersecurity present their recommendations about the IT policy reviewed in the earlier stage and get the IT policy and applicable standards, guidelines, and procedures approved by the VP-IT. This step is the last step for writing or updating applicable standards, guidelines, and IT policy procedures.
Publish and Communicate the Policy
At this step, the ITPCO publishes the approved IT policy and associated standards, guidelines, and procedures into the document repository from where stakeholders can access the new (or the latest version of existing) policy. In this step, when publishing documents, the use of metadata such as title, number, dates (published, revision, active, expiry), doc-state (as active or archived), and doc-status (as a draft or published) could facilitate searching existing documents for future revision or archival. At this step, using appropriate communication means, the ITPCO and representatives of the target stakeholders widely disseminate the new (or the latest version of existing) policy and applicable standards, guidelines, and procedures to all the stakeholders.
Implement the Policy and Provide Training
At this step, the ITPCO and representatives of the stakeholders implement the IT policy and provide the required training and awareness of the IT policy standards, guidelines, and procedures to all the stakeholders,
Monitor and Review Policies
At this step, the ITPCO ensures obsolete and older versions of the IT policies are archived or removed from the policy repository. If an existing IT policy was revised and published with a new version, the policy’s expiry date should be set accordingly as the latest version of the policy is published. Since the ITPCO is responsible for leading the monitoring, annual review, and analysis of existing policies, standards, and guidelines for continued pertinence and effectiveness, this phase could be triggered independently of a requirement for creating new (or revising an existing) policy.
References
AAU. (n.d.-a). AAU home page. Retrieved from Addis Ababa University: http://www.aau.edu.et/
AAU. (n.d.-b). AAU at a glance. Retrieved on December 12, 2020 from Addis Ababa University: http://www.aau.edu.et/aau-at-a-glance/
Alkhaldi, F. M., Hammami, S. M., & Ahmar Uddin, M. (2017). Understanding value characteristics toward a robust IT governance application in private organizations using COBIT framework. International Journal of Engineering Business Management, 9, 1.
Cunningham, J. A., Lehmann, E. E., Menter, M., & Seitz, N. (2019). The impact of university focused technology transfer policies on regional innovation and entrepreneurship. The Journal of Technology Transfer, 44(5), 1451. DOI: 10.1007/s10961-019-09733-0
Gover, J., Carayannis, E. G., & Peterson, M. (1996). Improving the national science and technology policy development process. IEMC 96 Proceedings. International Conference on Engineering and Technology Management. Managing Virtual Enterprises: A Convergence of Communications, Computing, and Energy Technologies, 168–174. DOI: 10.1109/IEMC.1996.547809
Han, J. (2018). Effects of technology transfer policies on the technical efficiency of Korean University TTOs. KDI Journal of Economic Policy, 40(4), 23–45. DOI: 10.23895/kdijep.2018.40.4.23
NCU. (n.d.). NCU cloud consulting services organization diagram. Retrieved on December 12, 2020 from https://ncuone.ncu.edu/shared/Course%20Interactives/ST/TIM-7040/week_04_Cloud_Consulting_Services/catalog_of_services.html
Siregar, A.H., Gevrazi, D.S, Putra, D.A., & Wicaksono, B. (2018). Policy evaluation of security system based on security camera technology in Batam City. IOP Conference Series: Earth & Environmental Science, 175(1), 1.
Tanaka, K., & Sakata, I. (2017). New science and technology policy evaluation using bibliometric approach. Portland International Conference on Management of Engineering and Technology (PICMET), 1–5. DOI: 10.23919/PICMET.2017.8125259
UM. (n.d.). IT Policy Development and Administration Framework. Retrieved on December 13, 2020, from Office of the vice president for IT & CIO: University of Michigan: https://it.umich.edu/information-technology-policies/policy-development-framework
Umaroh, S., & Kartika, A. D. (2018). A framework for an IT use policy development. Electrotehnica, Electronica, Automatica, 66(1), 159.
